Many organizations are ready and want to move forward with AI initiatives, but a growing number are running into the same problem early: their data isn’t ready. From data quality to governance, AI...
Nutanix AHV is gaining attention among enterprise IT teams as part of ongoing virtualization and infrastructure planning. AHV is Nutanix’s native hypervisor, delivered as part of the Nutanix Cloud...





































































/_blog/vlcm-syxsense.jpg)


















.jpg)






/_blog/netspi-us-partner-of-the-year-award-vlcm.jpg)






























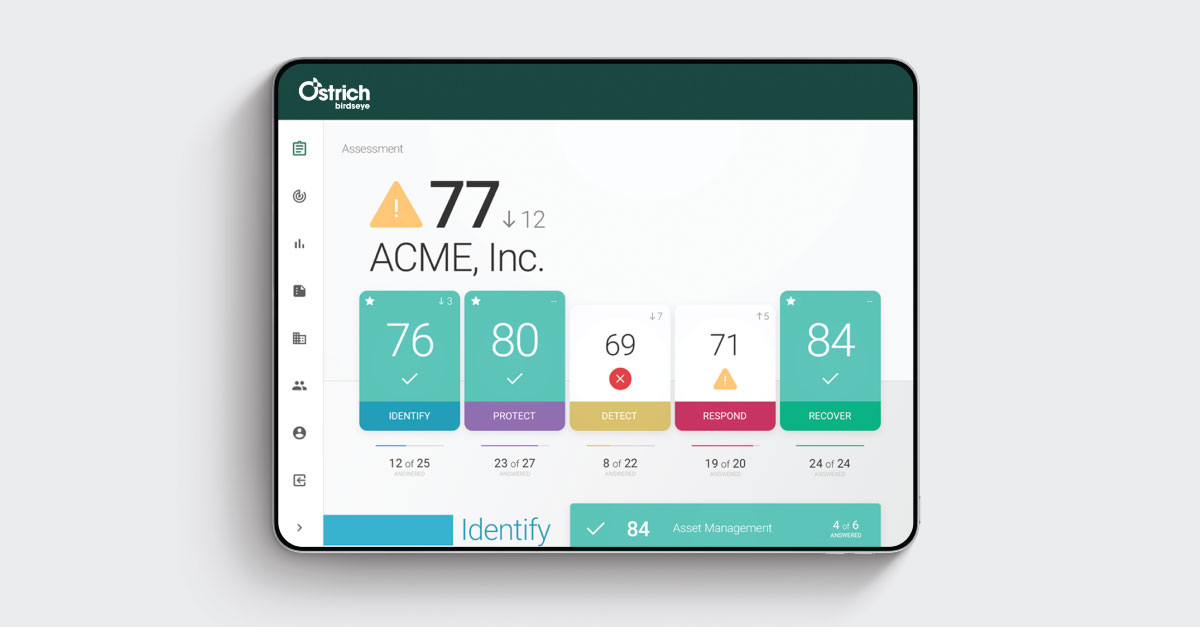









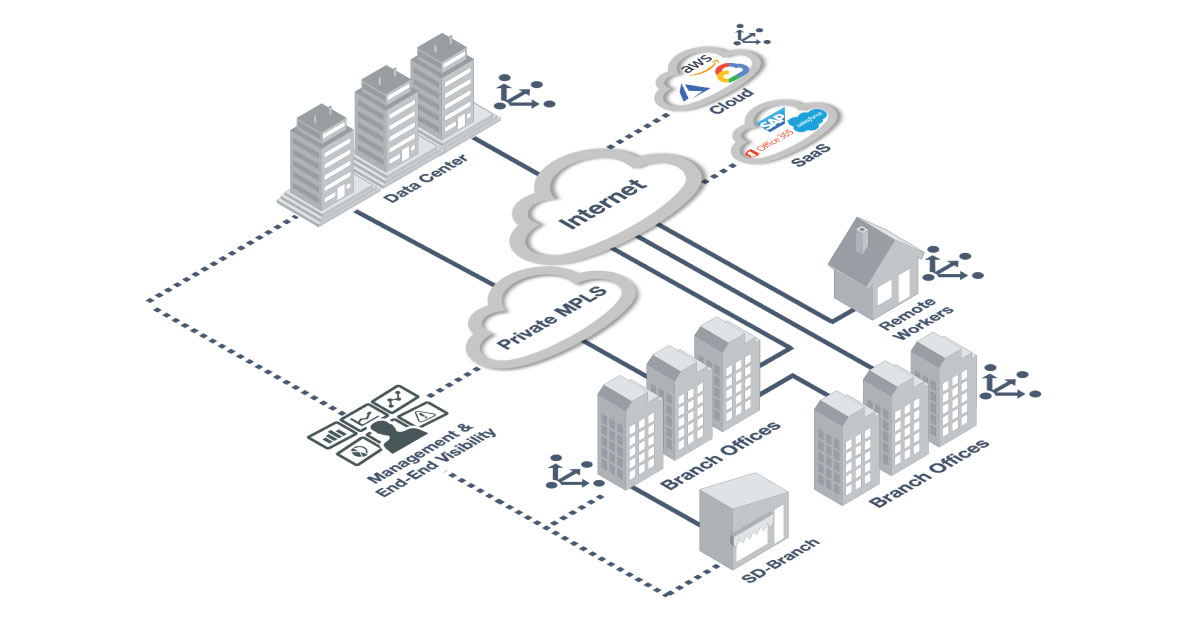











.jpg)


.jpg)















/_blog/HPE20170216009.jpg)





.jpg)



.jpg)