In the face of persistent IT disaster threats, the proactive protection of critical data is more essential than ever. Understanding and addressing this challenge involves equipping infrastructure with the necessary tools to prevent potential disruptions. A cornerstone in this protective framework is Veeam.
Recognized as a leader in data availability and backup solutions, Veeam offers a range of robust security features. These functionalities are tailored to safeguard data, sustain business operations, and aid disaster recovery (DR). This article provides insights into the maximization of Veeam's built-in security features to enhance defenses against IT disasters.
Veeam’s inherent security features
Veeam stands tall in the market with its rich array of data protection and security functionalities. Key built-in security features include data encryption, network traffic encryption, secure restore capabilities, data loss prevention, and multi-factor authentication. Let's dive into how these features enhance your disaster recovery strategy.
Data encryption
Veeam’s data encryption mechanism secures data at rest and in transit using AES 256-bit encryption. This isn't just about meeting a security benchmark—it's about providing robust, end-to-end protection. Whether your data is nestled within the storage repository or moving across networks, Veeam's rigorous encryption ensures it remains unreadable to unauthorized parties, thereby reducing the risk of data breaches.
Network traffic encryption
Veeam's approach to network traffic encryption distinguishes it in the security field. The encryption feature safeguards data in transit across potentially unsecured networks, reducing vulnerabilities during data transmission. This extra layer of protection helps ward off cyberattacks aiming to exploit data in transit.
Secure restore capabilities
Veeam goes a step further than many solutions with its Secure Restore feature. Not only does it facilitate data recovery, but it also allows IT administrators to conduct an antivirus scan before the restoration process. This preemptive measure ensures your recovered data is malware-free, thus creating a secure environment post-recovery. Moreover, Veeam's Secure Restore offers additional safety by preventing (re)infection from backup data that may harbor undetected latent malware, helping maintain the integrity of your broader dataset. It's not just about getting your data back—it's about ensuring that data is safe to use.
Immediate testing of security patches:
The dynamic landscape of cyber threats requires constant vigilance and swift response. Veeam equips you with the ability to immediately test day-zero patches against your data using Veeam DataLabs™ On-Demand Sandbox™. This feature significantly reduces your response time, mitigates the risk of infection, and helps ensure that your data can be protected from threats as soon as they appear. With Veeam, you're not just defending your data—you're staying a step ahead of potential threats.
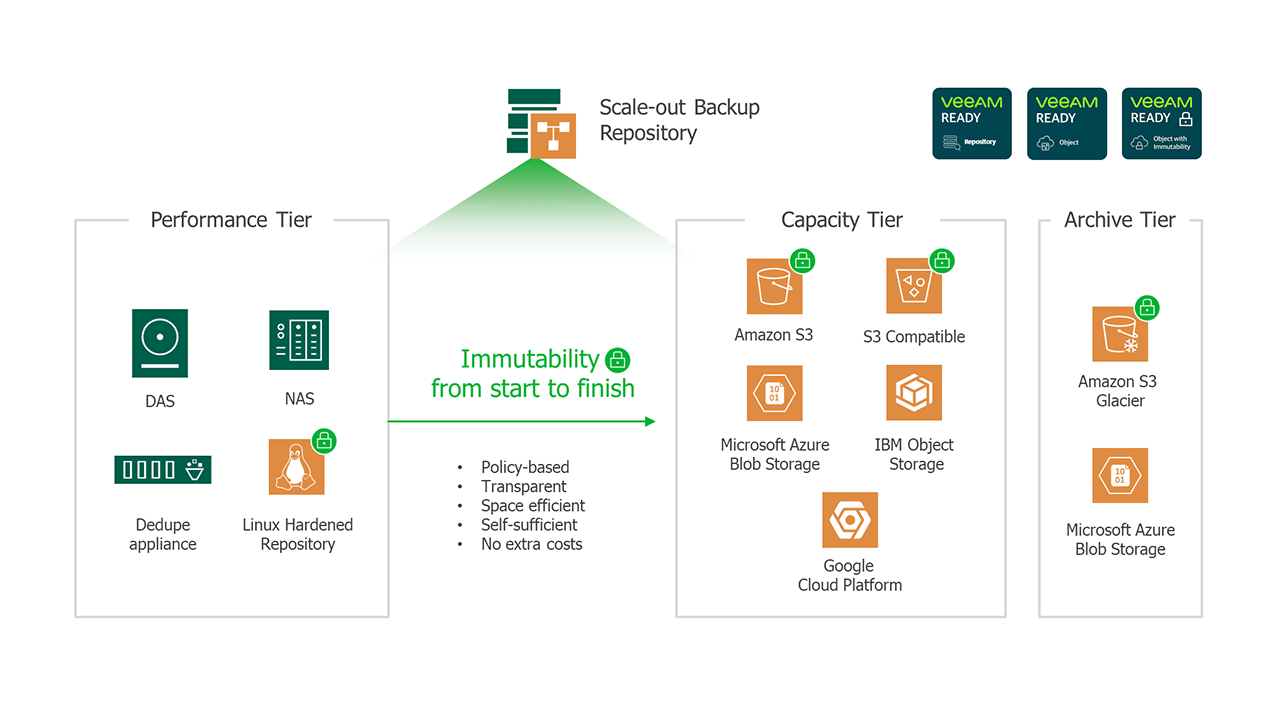
Immutable native backups:
Immutability in data backups is a powerful weapon in the fight against cyber threats, particularly ransomware. Veeam's Immutable Native Backups feature offers a level of data security that goes beyond traditional methods. It ensures that your backup data can't be altered or deleted until the defined retention period has passed. This stops ransomware in its tracks, ensuring backup compliance and safeguarding your recoverability with immutability for your backup copies. With Veeam, you're not just protecting your data—you're making it indestructible to attacks for a defined period.
How to implement Veeam’s security features for effective disaster recovery
After acquiring Veeam, it is important to utilize its security features optimally to strengthen your disaster recovery plan. Here's a simple step-by-step process to guide you:
Step 1: Develop a comprehensive disaster recovery plan
The primary step in leveraging Veeam's security features is to incorporate them into a broader disaster recovery plan. This plan should outline potential disaster scenarios, the responses to each, and how Veeam’s features can mitigate the impact of these disasters.
Step 2: Prioritize continuous data protection
Continuous data protection is one of Veeam's key features. By ensuring that the business has access to the latest data copies at all times, this feature significantly reduces data loss and improves the Recovery Point Objective (RPO) and Recovery Time Objective (RTO).
Step 3: Regularly test backups with Veeam’s SureBackup and SureReplica
Veeam's SureBackup and SureReplica are powerful tools that allow automated testing of your backups and replicas. Regular use of these tools verifies the recoverability of your backups, ensuring that your data can be successfully restored when disaster strikes.
This guide, while straightforward, serves as a foundation. Each step can and should be adjusted according to the specific needs and demands of your organization. Regular review and revision of the plan will ensure it remains effective against evolving threats.
Final Thoughts
Armed with Veeam's robust security features and an effective disaster recovery strategy, you can ensure your business continuity, even when faced with adverse circumstances. Remember that disaster recovery is not a one-time task—it's a continuous cycle of improvement. As the threat landscape evolves, so should your strategy, utilizing the full potential of Veeam's evolving capabilities.
In this journey, don't overlook the value of partnering with experienced IT solutions providers like VLCM. With expert guidance and hands-on assistance, VLCM can help you optimize your use of Veeam’s built-in security features and implement effective data protection and disaster recovery strategies. Moreover, consider taking advantage of Veeam’s training and certification programs, which equip your IT team with the latest best practices and techniques for using Veeam’s features effectively.
Proactivity is paramount in maintaining business operations amidst potential disasters. By leveraging Veeam’s powerful built-in security features effectively and adhering to the best practices outlined in this guide, you're not merely preparing for disaster—you're constructing a resilient foundation for your organization.
