
Now that it is 2022, it is safe to say that people are no longer asking “What is the cloud and where is it?” as most people and their data are now living there. We see increasingly that our clients are moving to the cloud at a rapid pace. Some clients have moved to a “hybrid cloud” where they have some services in the cloud and some on-prem still. This might also include having the data stores live on-prem and access to the data comes via some cloud application. Many clients have moved much of their workloads to either AWS, Google Cloud, or Azure. Some of our clients have even built their own “private” cloud resources. But what I have found is that most of our clients have “all of the above” selected as their answer.
As many of us understand what the cloud is, we still have different definitions for much of it. And when moving to the cloud we often wonder who owns what and who is responsible for what. Past that there are things like SaaS, IaaS, PaaS, and all kinds of other “aaS” stuff out there. All of this starts to create areas of grey or as I like to say it “turns your clouds into grey clouds”. And everyone knows what happens when grey clouds come rolling in. Rain is on its way, ruining your sunny day.
When considering cloud security, I like to break it down into a few areas of consideration.
- Define it: When you are talking about the cloud what exactly are you talking about. This I where the “aaS’ of our world comes into play. Are you talking about Software as a Service (SaaS)? Think about services like Salesforce.com or Adobe Creative Cloud. Or maybe you are talking about Platform as a Service (PaaS), think of AWS or App42. And then there is the possibility that you are talking about Infrastructure as a Service (IaaS) like AWS EC2, or Zscaler.
- Responsibility: Once you have defined it you need to understand what you are responsible for and what they are responsible for. This responsibility changes based on what type of cloud resource we are talking about. Below is a chart of these assumed responsibilities.
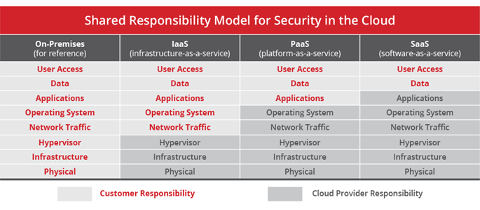
- Visibility: You have heard the term “Cloud Sprawl”. It sounds like something that a weathercaster might be talking about, but it is a real thing. With the ease of use and low cost of entry for cloud services, many of our clients find that they have no real idea of how many cloud assets and services they have in their environments. Different departments grab credit cards and start ordering up cloud services. Not even talking to the IT department, let alone InfoSec. Next thing you know you have multiple unmanaged workloads in the cloud that are connecting to assets that are in your environment. Causing unknown exposures and raising the overall attack surface of the company. With this unintended exposure, there are several new and emerging technologies that we help our clients understand and implement to gain this visibility.
- Harden: Identify some products or services that can help protect these cloud assets. This can come in different forms and different services. From products that can protect the individual workloads to products that can protect the accounts and network access.
We work with our clients to go through this process. Help them identify the best fit for the goals of the organization and secure their cloud environments. Contact us when you are ready, and we will be happy to review your cloud environments. Take advantage of our advisory cybersecurity services.
Jamie Maxfield
Sr. Cyber Security Engineer. Director of Technical Sales
LinkedIn: https://www.linkedin.com/in/jamie-maxfield-28765a3/
Read more from Jamie Maxfield: The Importance of Detection.
