
As the digital landscape widens, so does the breadth of security threats. Since the start of the pandemic, cyberthreats are up 400%, and businesses of all shapes and sizes are on the target list - not just enterprises. Small to medium-sized businesses (SMBs) are particularly vulnerable to security woes, whether it be low IT staffing levels or scarce or severely overstretched resources. In an environment where IT staff struggles to keep up, most SMBs find themselves forced to react to security alerts, rather than proactively and preemptively manage threats and address potential vulnerabilities. Thus, SMBs are at high risk for catastrophic damage or loss.
To help prepare SMBs for this challenging security landscape, today’s blog is centered on the top four security threats affecting SMBs in 2022, and what they can do to be more cyber secure without breaking the bank.
1. Ransomware
Ransomware is rogue software that encrypts business data and systems that can’t be recovered without paying for decryption - with no guarantee of success. For an SMB, ransomware can literally mean the end of your business. According to A 2020 survey from the Ponemon Institute, 47% of respondents do not have the ability to prevent and detect ransomware. In another survey from Forrester Research, the average ransomware incident lasts 7.3 days. Questions to ask:
- Can your business survive that long without access to its data or computers?
- Can your business afford a ransom payment?
2. Phishing
Phishing is email-, web page-, or social media-supplied links that take unwary users to malicious sites where passwords and credentials get stolen. In this particular security threat - employees are the weakest links in a company and the easiest to exploit. If your business lacks an IT team, your employees might not know how to spot a phishing attack. If you currently do not have the resources to teach your employees how to identify a phishing threat, Microsoft has a great, concise resource on how to protect yourself from phishing.
3. Data Leakage / Insider Threats
Data leakage is where business data gets past organizational safeguards and into the wrong hands. Data leakage can occur accidentally, i.e. an employee unintentionally selecting the wrong recipient when sending an email containing confidential data. It can be the result of a disgruntled or ill-intentioned employee - often using printers, cameras, photocopiers, USB drives, or even sifting through trash for documents. Data leakage can also come from phishing or social engineering attacks.
4. Hacking
Hacking takes the form of technical and social engineering attacks on IT infrastructures that aim to gain control; deny access or service; and steal data, intellectual property, or money. Over the years, hackers have become more and more sophisticated in their attacks. With operations now resembling organized crime syndicates, even trained employees sometimes find it hard to identify their hacking attempts. A way to help prevent a hack is to consistently keep on top of installations of the latest patches and updates for your hardware and software. Hackers keep track of security vulnerabilities for easy inroads into a company, so applying the most current patches is a reliable way to keep your company safe.
Baked-in security solutions for SMBs
While the above indeed may be overwhelming, our engineers here at VLCM recommend HPE security solutions to help SMBs offset staffing shortages, fill skill gaps, and speed response times. Here’s how HPE can help businesses like yours close security gaps:
- Data-centric security: Uses proven, NIST-standardized methods to protect data in use, at rest, and in motion (which meet U.S. Government and European Union GDPR requirements). It provides strong encryption and tokenization to render stolen data useless to attackers.
- Zero-trust security: Is a philosophical approach to identity and access management, whereby no user or software action is trusted by default. Thus, all users, devices, and application instances must prove their identities and authorizations conclusively before access is allowed.
- DevSecOps: Embeds security teams and concepts in a formal development process, designed to ensure security is addressed early and often along the entire app delivery chain (design-build-test-deliver-maintain), not simply bolted onto a “finished” system or service at the end of development. Security is addressed during development and deployment through a set of DevSecOps best practices (Figure 1).
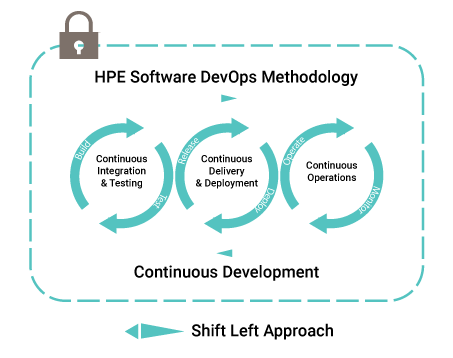
Figure 1: DevSecOps expands on the underlying concepts of DevOps to build the mindset that everyone is responsible for Security
- HPE Trusted Supply Chain Initiative: To meet the needs of customers with high-security requirements and challenging usage scenarios, HPE operates a Trusted Supply Chain. Such customers include U.S. federal and public sector consumers who prefer U.S.-sourced products with verifiable cyber assurance. Security is baked into the supply chain, by including additional hardened security features and assigning HPE employees to oversee products during the manufacturing process to vet all parts, observe assembly, and make sure packaged devices remain tamper-free until customers accept delivery. HPE includes an exclusive silicon root of trust that embeds silicon-based security into industry-standard servers and maintains security controls across its entire supply chain to establish and maintain stringent security at the hardware level.
The switch from reactive, static, and siloed security tools and techniques to intelligent, adaptive security platforms that span the digital world can happen. HPE’s security solutions allow SMBs to close existing security gaps with coverage at the edge, in the cloud, and on-premises, under a consistent and security umbrella.
Visit www.vlcm.com/contact-us to talk to one of our cybersecurity experts on how HPE can help your SMB be more cyber secure.
