The number of credential harvesting breaches that could have been prevented by enabling two-factor authentication (2FA) is staggering. Verizon’s 2017 Data Breach Investigation report indicates that 81% of hacking-related breaches leveraged either stolen and/or weak passwords. Yet less than 10% of Gmail users enable two factor authentication and less than one-third of people use 2FA. For companies that are required to comply with PCI, HIPAA, GDPR, etc. enabling 2FA could mean the difference between a failed hacking attempt or being subjected to substantial fines and penalties.
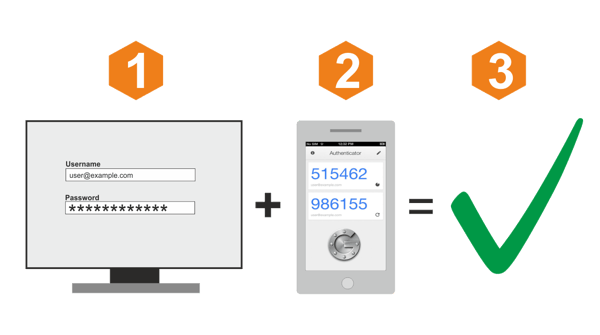
2FA is a method of confirming your identity by utilizing a combination of two different factors. Those factors are:
- Something you know like a password
- Something you have like a smartphone, or
- Something you are, like your finger print
Most companies that provide 2FA use something you know and something you have as their two factors for authentication, but we are starting to see more use of something you are.
2FA is type of multi-factor authentication (MFA), but I will leave MFA for a future discussion.
2FA is not new and has been around for a very long time. When you use your credit card (something you have) to make a purchase and are asked to enter your zip code (something you know) that’s 2FA.
To provide you another real word example, I will use LinkedIn’s method of 2FA. When I login to my LinkedIn account, I provide my password (something I know). LinkedIn then prompts me for a time limited PIN that is sent to my smartphone (something I have) via SMS text message. Once I enter that PIN, I have completed the 2FA process and I’m granted access to my LinkedIn account.
While many companies like Amazon, Apple, Facebook, Google, Microsoft, etc. provide 2FA, there are still many that don’t. You can find out which companies do or don’t provide 2FA by visiting twofactorauth.org. If a company you do business with does not provide 2FA, you can encourage them to do so using twofactorauth.org.
While 2FA does significantly enhance the security of your accounts, it’s not a panacea as 2FA using SMS text messages has become easier to compromise by social-engineering wireless carriers into forwarding text messages to another SIM card. Nor should 2FA be used as a crutch for weak passwords. There are stronger methods of 2FA such as the Google Authenticator app for Android and iPhone. The Google Authenticator app is very intuitive and makes using 2FA so much easier. Several companies like Facebook, Microsoft, Dropbox, etc. now support the Google Authenticator app for 2FA. Microsoft even offers a 2FA option for logging into their Office 365 suite of products and I highly encourage anyone using Microsoft Office to enable 2FA.
Using strong passwords and enabling 2FA will greatly enhance the security of your accounts and will provide you piece of mind, so just do it!
If you're interested in learning more about cyber security solutions to help your business, contact VLCM today for a free no-hassle consultation.
