
Recently I was in Park City, UT watching over 10 hours of soccer a day. Sitting in 98 degree heat, eating stale crackers, and listening to the soccer dads attempt to coach every member of both teams, was worth it to see my 16-year-old sister win the tournament. With the massive rise of soccer, I'm sure most of you can relate to cheering on a relative's soccer team to victory. Whether it's the tiny three-year-olds chasing the ball in a large mass, or a college team with exquisite technique, there is one thing in common: the need for a goalie.

As I watched my sister play in the championship game, their goalie got severely injured by a kick to the face. I started to think about what soccer would look like if there wasn't a goalie on one of the teams. It wouldn't matter how good your forwards were or how often they shot the ball; the likelihood of the goalie-less team winning would be next to zero.
The goalie is such an important member of a team, that even if a team had a goalie, but they were awful, the likelihood of that team winning would also decrease.
Some of our companies are like these goalie-less teams, attempting to secure a win without protecting our most valuable information.
98% of the cyber security industry has experienced a significant cyber threat in the past three years, and 58% took more than 24 hours to start remediation of the threat.
This is where cyber security comes in.
The trick, however, is that much like a soccer team, the opponent is always learning, adapting, watching game video, analyzing your technique, and finding the holes where they can strike.
Because of this, we need a new generation of cyber security tools to protect our companies.
Here is a list of VLCM's top-rated cyber security suggestions:

SentinelOne uses three phases of AI threat detection to protect your company: pre-execution, on-execution, and post-execution.
1. Pre-Execution: Uses a Static AI engine to provide pre-execution protection. Replaces traditional signatures and removes recurring scans that kill end-user productivity.
2. On-Execution: Behavior AI engines track all processes and their interrelationships, regardless of how long they are active. When malicious activities are detected, the agent responds automatically at machine speeds.
3. Post-Execution: Automated Endpoint Detection and Response provides rich forensic data and can lessen threat, perform network isolation, and protect the endpoints against newly discovered threats.
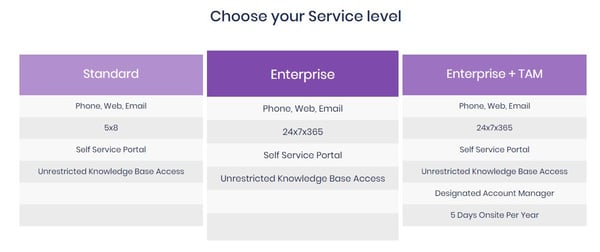
SentinelOne offers three different service level options pictured below:

Exabeam's game plan to protect you includes Collecting Unlimited Log Data, Detecting Threat Attacks, and Automating Incident Responses.
1. Collect Unlimited Log Data: The Exabeam security data lake combines a modern big-data infrastructure with predictable user-based pricing so you can collect and quickly search through all of your data sources in a central location without making compromises due to lack of scalability or budget.
2. Detect Complex and insider Threat Attacks: Exabeam’s User and Entity Behavior Analytics (UEBA) solution detects abnormal behavior and suspicious movements within your organization. Timelines of user and device behavior reduce the time and specialization required to detect attacker tactics, techniques, and procedures.
3. Automate and Orchestrate Incident Response: Exabeam’s incident response solution allows teams to respond to security incidents rapidly and with less effort than ever before using graphical playbooks and prebuilt AOI’s that connect and integrate all of your IT and security tools for an automatic response.

Guardicore is all about creating a map of both teams to better understand the strategy you need to use. Using Visualization, Micro-Segmentation, and Detection & Response, Guardicore gives you the full picture of the field.
1. Visualization: Guardicore Centra collects detailed information about an organization’s IT infrastructure through a mix of agent-based sensors, network-based data collectors, and virtual private cloud (VPC) flow logs from cloud providers. This information is then placed into context through a flexible and highly automated labeling process that includes integration with any existing data sources like orchestration systems and configuration management databases.
2. Micro-Segmentation: The detailed insights into application behavior can then be used to create granular micro-segmentation policies quickly through an intuitive visual interface. Centra’s micro-segmentation capabilities are also complemented by an innovative set of breach detection and response capabilities.
3. Detection & Response: Centra provides protection for your entire infrastructure. Centra protects workloads in hybrid environments with any combination of legacy systems, bare-metal servers, virtual machines, containers, and cloud instances in Amazon Web Services, Microsoft Azure, and Google Cloud Platform.

Check Point knows that tools and techniques that used to block the opponent don't work anymore. That's why Check Point's R80.10 uses Virtual Cloud Environments and Next Generation Policies to stay ahead of the other team.
1. Unified Management: With R80.10, access control and threat prevention management for all enforcement points are fully unified under the same console, removing the need to move between multiple interfaces. Unified management for both physical and virtual networks, on-premise or cloud enforcement points, ensures security consistency and full visibility into traffic across the network.
2. Automation: With the R80.10 API, security teams can automate any task or create web portals for security self-service.
3. Simultaneous Work: Concurrent administration now allows multiple administrators to work simultaneously on the same policy without conflict
4. Customization: This fully customizable dashboard allows you to focus only on what matters to you. You get a comprehensive view of your security posture, and can quickly drill down into incident or log details with a few clicks. Reports are easily tailored to for your stakeholders and accessible from any web browser.

ForgeRock keeps it about your customers. At its core, the ForgeRock Identity Platform uses real-time data and situational context to personalize and protect the customer experience. After all, we want our fans to see us win right?

1. Onmichannel: Accelerate customer engagement with an omnichannel experience: consolidate identity data of people, services, and things to create a consistent and unified profile across all digital channels.
2. Future-Proof: Future-proofed for the internet of things and next-generation identity management challenges: The platform connects, secures and manages millions of connected devices and things like cars, set-top boxes, wearables, and whatever’s coming next.
3. All-in-One: Designed as a unified architecture to eliminate integration costs and frustrations.
4. Lightweight & Modular: Internet-scale, all-inclusive functionality that you can turn on and off as needed.
5. Developer-friendly: The only unified offering CIAM solution to use a single, common programming interface (REST) that’s easy to invoke. The ForgeRock Identity Platform also leverages the latest DevOps models and best practices. Developers can easily build and maintain a production-grade, devops-enabled, referenceable, cloud ready architecture with Kubernetes. They can also automate multi-cloud deployments, with supporting DevOps practices using Docker for containers and Kubernetes as the orchestration platform.

It shouldn't matter where you are playing, the goalie should be able to block at both at-home and away games. That's why ThreatX is all about protecting your apps and apis anywhere. They use four steps to ensure victory:
1. Easily Deploy: Block cyber threats in hours with SaaS, on-prem, or Docker native-cloud deployment in your private cloud or provider (AWS, Azure).
2. ID and Profile Cyber Threats: IP fingerprinting, and application and attack profiling continually combine and correlate to identify, track and assess threat actors.
3. Neutralize Cyber Threats: Based on attacker profiling, detect and neutralize with high precision, layer 7 attacks, OWASP Top 10, bots, DDoS, and zero-day threats
4. Analyze and Optimize: Collective cyber threat intelligence combines with a managed service for 24x7 proactive monitoring and response.

Just like the name implies, Idaptive is all about adapting to the threat, whether they be a player from a foreign country, or an internal threat. Idaptive uses Single Sign-On, Multi-Factor Authentication, Account Provisioning/Deprovisioning, and Real-Time Analytics to create game plans.
1. Single Sign-On: Idaptive lets you deploy browser-based apps, native mobile apps and custom apps — all with a single username and password, controlled by IT, and leveraging industry standards such as SAML.
2. Multi-Factor Authentication: Choose from a comprehensive range of authentication methods, including passwords, smart cards, soft tokens, or cryptographic devices. Get the protection you need without sacrificing the convenience your users demand. Whether it’s a push notification, Idaptive mobile authenticator, SMS/text message, email, interactive phone call, YubiKeys , USB devices, digital certificates, Smart Cards, derived credentials or biometrics, Idaptive's got something for everyone.
3. Account Provisioning/Deprovisioning and Workflow: Automatically route application requests, create application accounts, manage entitlements within those accounts, and revoke access when necessary. Provision access across cloud, mobile and on-premises applications all from a central control point.
4. Real-time Analytics: Prioritize alerts based on risk and easily identify compromised accounts and stop threats in progress with a broad set of enforcement points. Remediate Suspicious Activity Through Anomaly Alerts. Risk-based policy can be enforced in real time at the point of access, where high-risk threats can be blocked.

Sometimes games are so intense, you need to bring in the Secret Service to protect the perimeter, or in this case the Secret Server. Thycotic's Secret Server lets you'
- Establish a Secure Vault to store privileged credentials in an encrypted, centralized vault.
- Discover Privileges to identify all service, application, administrator, and root accounts to curb sprawl.
- Manage Secrets through provision and deprovision, ensuring password complexity, and rotating credentials.
- Delegate access by setting up RBAC, workflows for access requests, and approvals for third parties.
- Control Sessions by implanting session launching, proxies, monitoring, and recording.
- All features demonstrated are provided whether you choose to deploy your privileged access management in the cloud or on premise – so you never have to compromise based on your deployment.
VICTORY!!

Let's get a win for our companies.

